Difference between revisions of "Dom0 Disaggregation"
From Xen
ToddDeshane (talk | contribs) (add references) |
ToddDeshane (talk | contribs) (fix placement of image) |
||
| Line 3: | Line 3: | ||
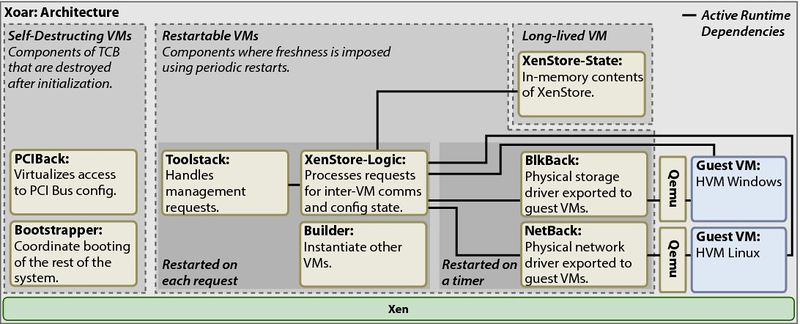
The [[Dom0]] or control domain has traditionally been a monolithic privileged virtual machine. However, the original intention was for Dom0 to be carefully broken into several privileged service domains - termed Dom0 disaggregation. Qubes OS, Citrix XenClient, and Xoar have made the case for more disaggregation of Dom0 for purposes of better security, reliablity, isolation, and auditability. |
The [[Dom0]] or control domain has traditionally been a monolithic privileged virtual machine. However, the original intention was for Dom0 to be carefully broken into several privileged service domains - termed Dom0 disaggregation. Qubes OS, Citrix XenClient, and Xoar have made the case for more disaggregation of Dom0 for purposes of better security, reliablity, isolation, and auditability. |
||
| + | [[File:Xoar_architecture.jpg|800px]] |
||
==References== |
==References== |
||
| Line 9: | Line 10: | ||
* http://www.cs.ubc.ca/~andy/papers/xoar-sosp-final.pdf |
* http://www.cs.ubc.ca/~andy/papers/xoar-sosp-final.pdf |
||
| + | |||
| − | [[File:Xoar_architecture.jpg|800px]] |
||
[[Category:Security]] |
[[Category:Security]] |
||
Revision as of 16:58, 6 April 2012
Dom0 Dissaggregation
The Dom0 or control domain has traditionally been a monolithic privileged virtual machine. However, the original intention was for Dom0 to be carefully broken into several privileged service domains - termed Dom0 disaggregation. Qubes OS, Citrix XenClient, and Xoar have made the case for more disaggregation of Dom0 for purposes of better security, reliablity, isolation, and auditability.